Our ISO27k certification journey, and beyond
The steps we took to achieve our ISO/IEC 27001 (including ISO/IEC 27018) certification and why it's so important to our business.

Introduction
In this post I’m going to tell you about our journey and why it is important to us achieving ISO/IEC 27001 certification. ISO/IEC 27001 or ISO27k is the international information security standard that provides the specification of control requirements for best practice information security management system (ISMS). It has become the most recognised standard for information security globally.
Achieving accredited certification to the standard provides an independent, expert assessment that our information security is managed in line with internationally recognised best practice and it proves our commitment to information security.
Early 2018 after doing our research into the standard we set off on our certification journey and on 20th December 2018, we received our first ever ISO/IEC 27001 certificate, awarded by Approachable. The decision to embark on our ISO27k certification journey was initiated by our founders, but the achievement can be put down to a fantastic team effort, something we are all very proud of!
In addition, we also felt it was important for Audiogum as we are fully cloud based to include ISO/IEC 27018, which is a code of practice for the protection of personally identifiable information (PII) using public cloud providers, acting as PII processors. Although it isn’t currently possible to be certified to ISO/IEC 27018, we included it as part of our ISMS and audit scope thereby certifying it.
A little context into why
There are many reasons why Audiogum decided to embark on this journey, you can read about in our Security & Compliance post but in essence, it was twofold:
For our existing or potentially new customers, we wanted to be able to demonstrate our commitment to information security, implementing security best practices across our organisation providing a common understanding of our security posture for them.
As Audiogum has grown and developed its services, internally we wanted to get that “rubber stamp of approval” that we were doing things in the right way and could confidently say so.
Our journey to accreditation
Since Audiogum started, we used our many years of combined experience to do things the right way, building up our business while implementing best practices, solid engineering principles and of course taking data privacy and security seriously right from the start.
We knew that we were in a good position but needed help in translating what we did into meeting the control requirements of the standard. We drafted in the assistance of IT Governance who were a tremendous help by providing us with templates, guidance and supported us as we implemented our management system.
Identifying assets and risk assessments
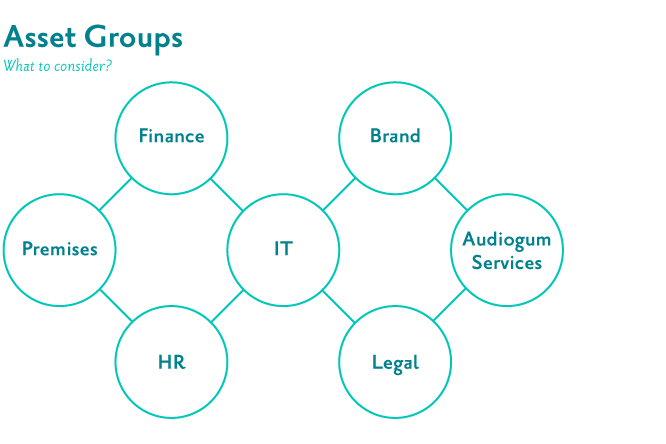
We set out by listing all of our assets which we described as something that has a value to Audiogum. By value, it is not just assets with an associated monetary value like IT equipment but also what has a perceived value for example, intellectual property, brand value, personnel records, services we built, etc.
We then grouped these assets producing a mind map that would later underpin our risk assessment process.
We then undertook the mammoth task of conducting risk assessments by asset creating our risk register. Each risk is treated (treatment plan) to bring the residual risk rating to below our risk tolerance and appetite threshold. To help explain this better, here is an example of an actual risk we identified related to data synchronisation between our regional deployments.
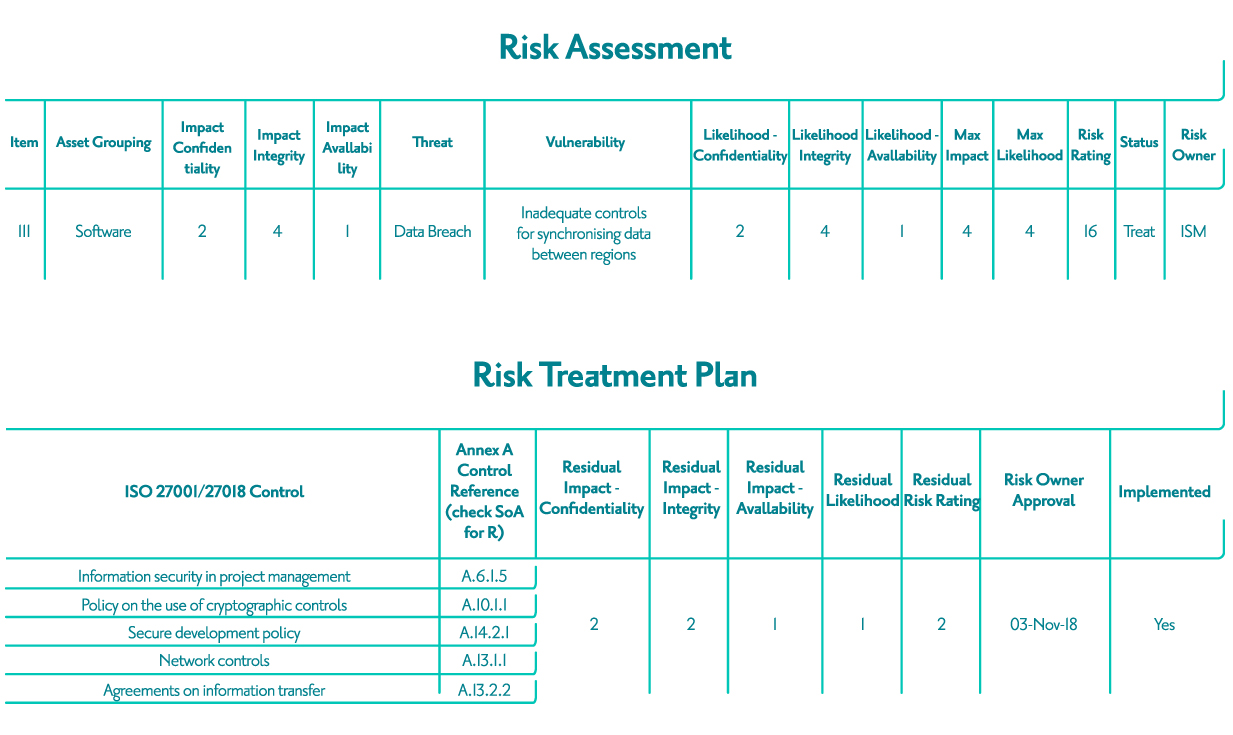
As you can see from the above risk, it has been treated using various Annex A controls.
Going through this process we created a backlog of stories. From the above risk, we created stories for updating our projects onboarding process, implementing physical network controls and writing new or updating existing policies.
Implementing our ISMS
As you can imagine, conducting risk assessments produced an overwhelmingly large backlog of stories that we tackled head on. During this time, we conducted weekly review and planning sessions ensuring we were all on the same page and maintained a common understanding of our management system.
It all started coming together and we were able to produce our Statement of Applicability (SoA). A SoA is one of the key documents that identifies the controls we selected to address the risks that were identified during our risk assessments, explains why the controls have been selected and states if they have been implemented.
Knowledge sharing and staff awareness
Since ISO27k affects everyone we wanted to make sure it was simple for employees to be able to find the information they were looking for, whether this was what their responsibilities were towards information security, how to navigate the ISMS and find information or even how to answer unknown questions an auditor might ask them when interviewed.
For responsibilities, we set up a database and a query tool (Metabase) that employees could use to query what their responsibilities are related to their role, their team or any other roles or teams.
We used our weekly Show & Tell meetings to present material on the ISMS implementation progress, what had been done, policy changes, working practices & guidelines and general information on ISO27k.
We held an ISO & pizza and an ISO fest interactive sessions where staff were presented with an overview of ISO27k, given dedicated time to read policies, ask questions and discuss any concerns or issues they may have had.
We ran two open book quizzes prior to the internal audits to test what everyone knew. Conducting these quizzes was brilliant enabling us to gauge our staff awareness and audit readiness using the quiz results to identify any areas we needed to focus on.
We created a dedicated #iso27k channel on Slack, our company messaging platform, that has useful links pinned to it, questions could be asked that we would all learn from and a platform for sending out ISO27k related notifications.
A “what to expect from the auditor” session was held where we went through some do’s and don'ts of being interviewed by an auditor.
We hold a monthly company meeting where ISO27k was always on the agenda providing additional updates to everyone on the project status.
Our design team came up with some eye-catching posters for the office, that provide a visual reminder to staff of key policy points.

We came up with some catch phrases to assist the mindset shift:
- New & Do - if it’s new - do something for example, if you purchase new hardware - do compliance checks, onboarding a new provider - do compliance checks, etc.
- See & Say - if you notice something that is not quite right, mention it in our #iso27k slack channel for example, policy wording incorrect, process has changed, data breach, etc.
- Say & Do - say what you do and do what you say.
- I SO 💙 ISO - simple but very effective.
Audits, non-conformities and opportunities for improvement
Probably the most daunting yet most valuable aspect of this journey was being audited. Our first internal audit was conducted where numerous non-conformities (NCR’s) and opportunities for improvement (OFI’s) were identified. All of these were captured on our improvement log and stories added to our backlog. Although at the time, we felt like we were stood up in front of the Spanish Inquisition, the audit highlighted gaps we had and areas we could improve on.
After our first internal audit, we scheduled a second so we were able to see if we were ready for our external audit once all NCR’s and most OFI’s were addressed. We were pleased to see that all of our hard work had paid off and the second internal audit only raised a couple of NCR’s and OFI’s. Now we felt confident and ready for our external stage 1 & 2 audits.
When it came to our stage 2 external audit, we were over the moon to have no new NCR’s, only two OFI’s raised and would be recommended for certification!
Going operational
The journey to accreditation may be over now that we are certified but it doesn’t stop there. Our management system is continuously improving and evolving keeping up to date with changes in our business and the services we offer.
Gearbox and objectives
We have set up a Gearbox & Objectives process that enables us to monitor progress of our objectives according to an agreed cadence. A gearbox item is a KPI with SMART measures agreed for each, who is responsible for it, what is the monitoring frequency, last and next review dates and the achievement status.
We have automated this by adding a story (repeater card) at the top of our backlog at the start of the month for every gearbox item that is due that month. Once it is on the backlog, it gets picked up and worked on as part of our normal day-to-day.
Monthly status
A monthly status report is produced that is reviewed and approved by our Operational Team (OT). The OT is the name we use for our Leadership Team that is made up of company founders and senior staff.
The status report is an important part of our performance evaluation and includes all the necessary status and data on the performance of our management system.
Templates, checklists and matrices
To help make things easier, we use templates, checklists and matrices wherever we can which not only act as a reminder of what needs doing before starting something new (remember the catchphrase New & Do), having them in place ensures there are no surprises further down the line when it might be too late.
Some examples of our key templates, checklists and matrices include:
- Project and suppliers onboarding templates.
- New starters and leavers checklists.
- Asset & Tool access control matrix.
- Classification, labelling and handling matrix.
Summary
ISO27k is part of our everyday thinking and keeps information security at the forefront of everything we do.
Audiogum gaining ISO/IEC 27001 including ISO/IEC 27018 accreditation means:
- We have demonstrated a commitment to security by everyone.
- We’ve adopted a risk based approach to making security decisions.
- We have implemented security best practices according to an internationally recognised standard across our entire organisation.
- We can confidently say we offer secure and compliant services.
If you would like to know more about the services we provide that can help you on your compliance journey, please get in touch.
